Discover how our product can help you and learn more about all the possibilities.

Beyond the Perimeter: managing cyber risks hidden in your third-party ecosystem
In today’s hyper-connected business environment, your cybersecurity is only as strong as the weakest link in your digital infrastructure. Learn how to see beyond your perimeter.

Building trust at scale: risk governance in the digital supply chain
Most of disruptions in global supply chains over the last five years were digitally sourced. Every connected supplier or cloud service becomes a potential vector for attack.

Cyber risk reporting for executives: communicate security in business language
Security managers must be able to translate technical complexity into understandable business language. Well-written risk reports enable the problem to be successfully presented to the highest levels of the company.
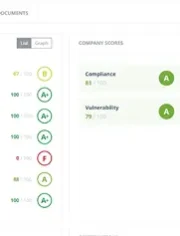
Cyber risk scoring: building a culture of measurable risk
Cyber risk scoring not only helps manage security more accurately, but also builds a measurable risk culture, where all areas, whether technical or business-related, share the same language, assessment and prioritisation.

Exposed and unaware? Reducing your external attack surface before it becomes a target
67% of organisations underestimate the actual number of assets accessible on the internet. Control your external attack surface, protect your organisation.

From compliance chaos to strategic control: how to navigate global cybersecurity regulations and third-party risk with confidence
Cybersecurity regulatory compliance has become one of the most pressing challenges for organisations worldwide. The key is not to aspire to reduce regulatory complexity but to make compliance a lever for strategic control and business resilience.
Download Whitepaper
Please enter your email address, and we’ll send you a message with the download link for the whitepaper.
